TryHackMe – Vulnversity – Complete Walkthrough
 Mehmet
27.03.2023
Mehmet
27.03.2023
This room uses one target virtual machine. You can deploy it using the green ‘Start Machine’ button at the top of Task 1. You’ll also need an attacking machine. This can be a machine that you set up and connect to TryHackMe via OpenVPN, or you can use the AttackBox. You can launch the TryHackMe AttackBox using the blue ‘Start AttackBox’ button at the very top of the page.
Question 1:
Deploy Machine
Answer 1:No answer needed
This room uses one target virtual machine. You can deploy it using the green ‘Start Machine’ button at the top of Task 1. You’ll also need an attacking machine. This can be a machine that you set up and connect to TryHackMe via OpenVPN, or you can use the AttackBox. You can launch the TryHackMe AttackBox using the blue ‘Start AttackBox’ button at the very top of the page.
Question 1:
There are many nmap “cheatsheets” online that you can use too.
Answer 1:No answer needed
Question 2:Scan the box, how many ports are open?
The Task tells us to perform a service version scan against the target using nmap:
Ordinarily I would try running an all ‘-A’ scan instead of a ‘-sV’ scan because it includes everything that the ‘-sV’ scan does as well as performing OS detection, traceroute, and a default script scan. In general I also like to speed the scan up using the ‘-T4’ option. In this case, I performed the scan exactly as prescribed by TryHackMe for the sake of this walkthrough:
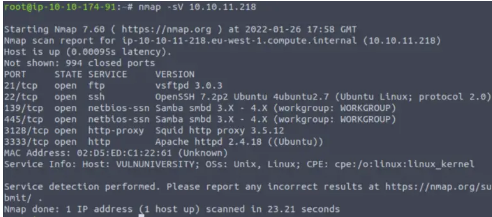
Nmap gives us a list of open ports and its best guess about the services and versions running on those ports. For example, we can see that the first open port is 21 which is running FTP (file transfer protocol). The version of FTP that nmap has detected is ‘vsftpd 3.0.3’. To answer the question, just count the number of open ports.
Answer 2:Highlight Below
We can see that our gobuster scan returned four results: /css, /images, /internal, and /js.
We can use a browser to navigate to each of the. To answer the question, we need to find the one that contains an upload form:
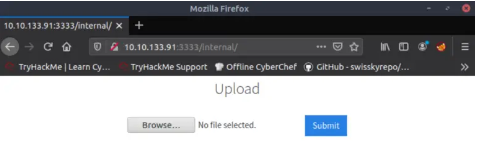
Question 1:
What is the directory that has an upload form page?
Answer 1:/internal/
Recap: We used nmap to identify an http server on port 3333, then used gobuster to identify directories. We found an upload form at http://
Upload forms often present vulnerabilities that can be exploited. When we encounter an upload form, we want to start testing it by seeing what is allowed and what isn’t.
Now that we have identified an upload form, we can try to exploit it.

Question 1:
What common file type, which you'd want to upload to exploit the server, is blocked? Try a couple to find out.
It’s always a good idea to have a look at the source code, which can provide hints as far as how we can proceed.
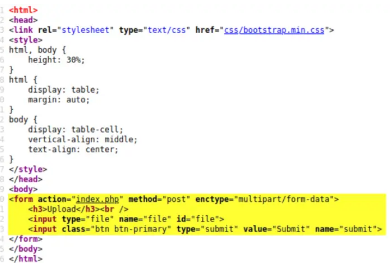
The form element that is being used to attempt an upload relies on an index.php file. Knowing this, we can theorize that we might need to use a php reverse shell to continue. A reverse shell is when we get code to run on a remote machine that connects back to our own machine to give us a shell.
One of the most popular php reverse shells is the pentest monkey shell, which can be obtained here. Download the zip file using the green ‘Code’ button and extract it.
Before we proceed to test the upload form, we’ll need to change the IP address in the php reverse shell script. Set this to your attack machine’s IP address:
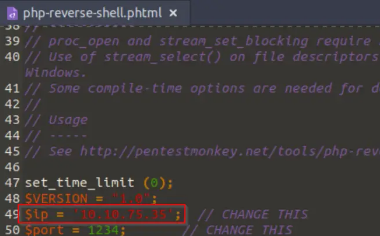
You can also change the port if you’d like; this is a matter of preference. We just need to make sure that our listener is set to the same port.
Next I like to start up a netcat listener so that I will have a shell as soon as the php file is executed. Do this in a terminal:
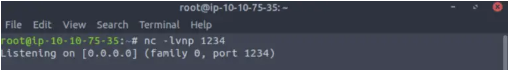
You can see that the port specified ‘1234’ in the listener is the same port in our php reverse shell code.
Let’s try uploading this using the form!
We get an error that says ‘Extension not allowed’:
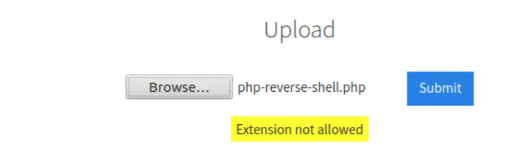
OK, so .php files aren’t allowed…maybe this is the answer to the first question.
Answer 1:
.php